Imperva’s DIY syslog format
I have had the fortune to support a few WAF installations, my preference is Imperva’s WAF solution. For any security product, being able to know what it’s doing and what is going on within the product is as important as the actual security being provided.
One of the features of Imperva’s solution that I find tremendously useful in an enterprise setting, and possibly an MSSP as well, is the ability to construct custom syslog formats for triggered alerts and system events in almost any format. I like to think of this as a Do-It-Yourself syslog formatter because the feed can be built and sent anywhere, using any number of options. More importantly, the feed can be bundled with specific policies or event types to provide limitless notification possibilities that often require professional services engagements to develop and implement.
In Imperva terminology, any policy or event can be configured to trigger an “Action Set” containing specific format options for among other things syslog messaging. If your logging platform (PLA) or SIEM requires a specific format, there’s a very strong chance that, with no more effort than building a policy, you can build the ${AlertXXX} or ${EventXXX} constructs necessary for your needs.
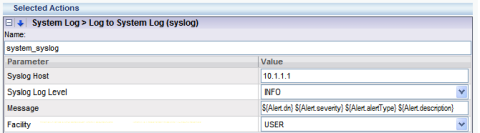
You can model the alerts to look like the Cisco PIX format, ARCSight’s CEF format can be used, or you can make your own as I’ve done in this screenshot:
In addition to allowing customized messaging format, Imperva’s SecureSphere platform allows unique message formats and destinations to be specified at the policy and event level. For example, a “Gateway Disconnect” or ” throughput of gateway IMPERVA-01 is 995 Mbps” message can be sent to the NOC’s syslog server for response, while XSS or SQL Injection policies can be directed to a SOC or MSSP for evaluation. Additionally, the “Action Set” policies can be setup so that the SOC is notified on both of the messages above as well as security events.
The configuration of the custom logging format is very straightforward, using placeholders to build the desired message format. The document “Imperva Integration with ARCSight using Common Event Framework” provides a number of examples, including a walk-through for building a syslog alert for system events, standard firewall violations, as well as custom violations. The guide is directed at the integration with ARCSight.
Depending on the version of Imperva SecureSphereyou are running / evaluating, the alert aggregation behavior will differ. Newer versions (6.0.6+) better support SIEM platforms with updated alert details, where older versions push syslog events on the initial event only.
You can request a copy of Imperva Integration with ARCSight using Common Event Framework to get additional ideas on customizing your syslog feeds for your SIEM product.
Posted on June 9, 2009, in How to's, Security Management and tagged Firewall log, Log Analysis, security, Security Management, SIEM, WAF. Bookmark the permalink. 5 Comments.
First of all, good job on this blog, very informational!
Hey where is this document that you have mentioned?
** The document ”Imperva Integration with ARCSight using Common Event Framework” provides a number of examples **
I couldnt find it on google…
Is there any way you could publish it or send me via email?
Thanks!
I am having a problem viewing your page correctlly through the latest version of Opera. It’s fine in IE6 and Firefox though.
So, the absence of a TCP syslog in Imperva didn’t bother you then?
Who ever deploys UDP only syslog systems these days? Just another half-finished feature if you ask me…..
Thanks Rubbish — I’m confused by your comment.
You can not only send TCP-based syslog events from the Management platform over a port of your choice in a format of your choice, but the actual security gateways themselves can syslog via TCP straight to two (2) different logging servers.
This is configurable from the Management server GUI’s Setup -> Gateways tab.
I’m not a big fan of logging directly from the security devices to both a management platform and a separate log collector, but the option is there if you get bored!
Howdy This is great info, am intrested in it… gud sh!t m8